Windows UI Automation exploited to bypass EDR tools, enabling data theft, phishing, and app manipulation.
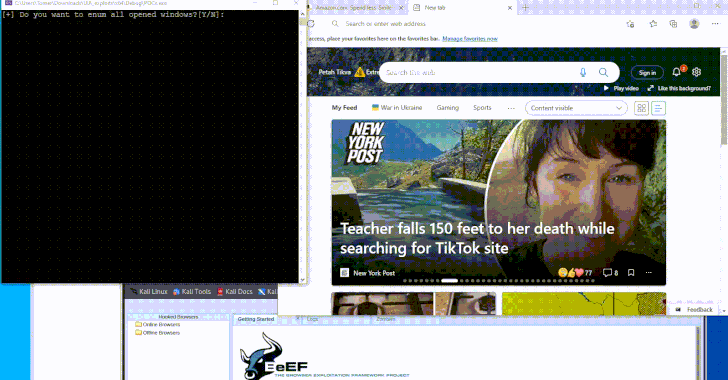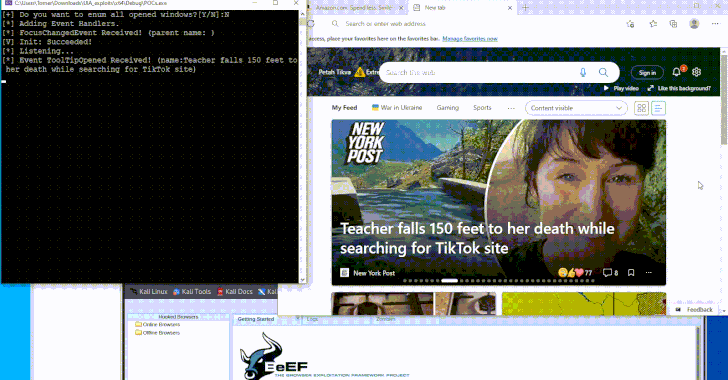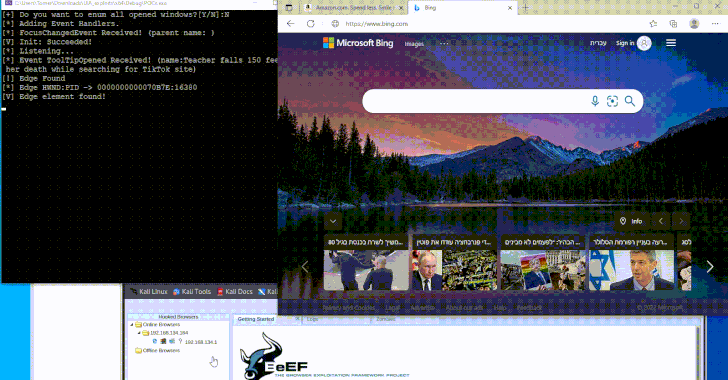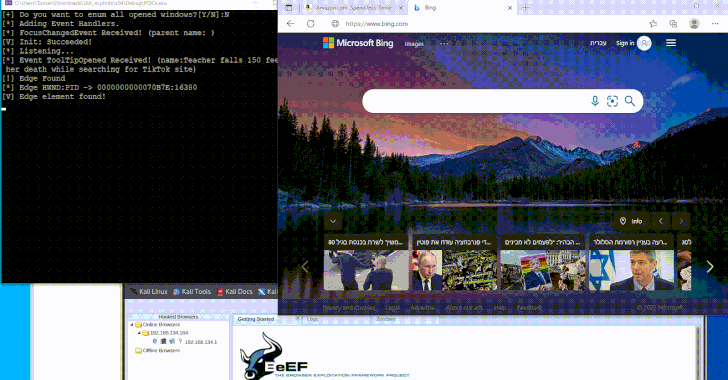


Phishing gang arrested in Belgium and Netherlands; Europol seizes luxury goods, cash, and millions stolen.
Humanity’s quest for answers has a new ally: Google’s Willow chip — a quantum chip that outpaces the fastest supercomputers by septillions of years! Imagine solving problems regular computers take years for—like creating life-saving medicines, predicting weather, or designing tech we haven’t dreamed of yet. But with great power comes challenges: high costs, logistics, and even risks to cybersecurity. The quantum revolution has begun, but the big question is—how will we use this power? Palki Sharma tells you.
Google | willow | quantum chip | firstpost | world news | news live | vantage | palki sharma | news.
#google #quantumchip #willow #firstpost #vantageonfirstpost #palkisharma #worldnews.
Vantage is a ground-breaking news, opinions, and current affairs show from Firstpost. Catering to a global audience, Vantage covers the biggest news stories from a 360-degree perspective, giving viewers a chance to assess the impact of world events through a uniquely Indian lens.
The show is anchored by Palki Sharma, Managing Editor, Firstpost.

Mike has over 15 years of experience in healthcare, including extensive experience designing and developing medical devices. MedCrypt, Inc.
On October 1, 2024, the Food and Drug Administration (FDA) marked a major milestone in medical device cybersecurity enforcement. This marks one year since the retracted Refuse to Accept (RTA) policy and the full implementation of the Protecting and Transforming Cyber Healthcare (PATCH) Act amendment to the Food, Drug & Cosmetic Act (FD&C). The FDA’s new requirements represent a fundamental shift in the regulatory landscape for medical device manufacturers (MDMs), as cybersecurity is now a non-negotiable element of device development and compliance.
The timing is not coincidental. In 2023, the FDA issued its final guidance entitled “Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions.” This outlined the detailed cybersecurity requirements and considerations that MDMs must address in their submissions, highlighting the security measures in place to gain regulatory approval. With these requirements, the FDA is taking a hard stance: Cybersecurity is a core consideration, with compliance being systematically enforced.

Cybersecurity firm McAfee says it’s identified a “significant global increase” in a smartphone hack that triggers extortion, harassment and drains bank accounts.
McAfee says hackers are increasingly deploying a group of malicious financial apps containing “SpyLoan” malware, posing a serious threat with more than eight million active installations around the world.
The apps are on Google Play and use the names, logos, brand colors and interfaces of well-known financial institutions.


In this respect, I believe regulators have fallen short. In a world facing ongoing cyber threats, the standards for cybersecurity are set surprisingly low that their rules typically only recognize encryption of all stored data as a requirement. This is despite the fact that encryption—not firewalls, monitoring, identity management or multifactor authentication—is the purpose-built technology for protecting data against the strongest and most capable adversaries. Stronger regulations are needed to ensure encryption becomes a mandated standard, not just an optional recommendation.
Fortunately, companies need not wait until regulators realize their folly and can opt to do better today. Some companies already have. They approach data security as an exercise in risk mitigation rather than passing an audit. From this perspective, data encryption quickly becomes an obvious requirement for all their sensitive data as soon as it is ingested into a data store.
Another beneficial development is that encryption has become easier and faster to implement, including the ability to process encrypted data without exposure, a capability known as privacy-enhanced computation. While there will always be some overhead to adopting data encryption, many have found that the return on investment has shifted decisively in favor of encrypting all sensitive data due to its substantial security benefits.