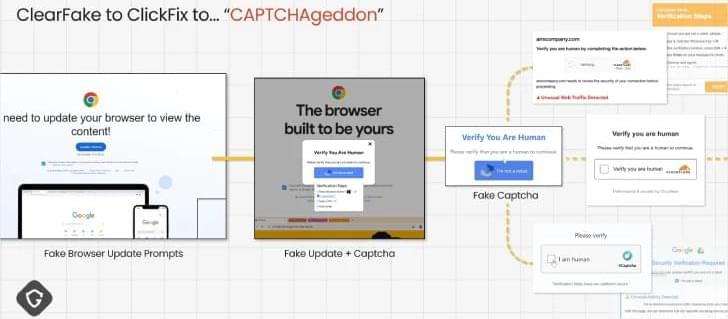
Ukraine’s CERT-UA warns of UAC-0099 and Gamaredon phishing attacks using custom malware and social lures.







A newly discovered Linux malware, which has evaded detection for over a year, allows attackers to gain persistent SSH access and bypass authentication on compromised systems.
Nextron Systems security researchers, who identified the malware and dubbed it “Plague,” describe it as a malicious Pluggable Authentication Module (PAM) that uses layered obfuscation techniques and environment tampering to avoid detection by traditional security tools.
This malware features anti-debugging capabilities to thwart analysis and reverse engineering attempts, string obfuscation to make detection more difficult, hardcoded passwords for covert access, as well as the ability to hide session artifacts that would normally reveal the attacker’s activity on infected devices.

Ransomware gangs have recently joined ongoing attacks targeting a Microsoft SharePoint vulnerability chain, part of a broader exploitation campaign that has already led to the breach of at least 148 organizations worldwide.
Security researchers at Palo Alto Networks’ Unit 42 have discovered a 4L4MD4R ransomware variant, based on open-source Mauri870 code, while analyzing incidents involving this SharePoint exploit chain (dubbed “ToolShell”).
The ransomware was detected on July 27 after discovering a malware loader that downloads and executes the ransomware from theinnovationfactory[.]it (145.239.97[.]206).

A threat actor has been abusing link wrapping services from reputed technology companies to mask malicious links leading to Microsoft 365 phishing pages that collect login credentials.
The attacker exploited the URL security feature from cybersecurity company Proofpoint and cloud communications firm Intermedia in campaigns from June through July.
Some email security services include a link wrapping feature that rewrites the URLs in the message to a trusted domain and passes them through a scanning server designed to block malicious destinations.