A pulsar’s gentle twinkle is revealing how space quietly bends and delays the signals we receive from the cosmos.






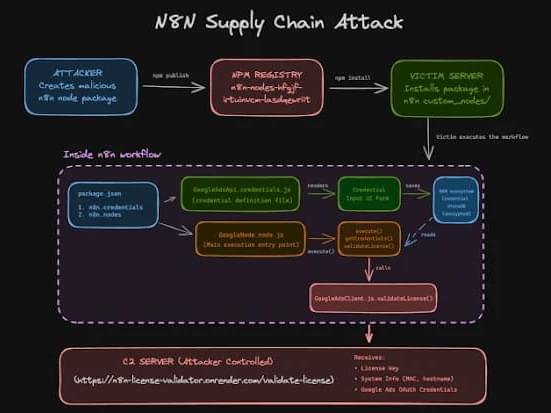
N8n has also warned about the security risk arising from the use of community nodes from npm, which it said can introduce breaking changes or execute malicious actions on the machine that the service runs on. On self-hosted n8n instances, it’s advised to disable community nodes by setting N8N_COMMUNITY_PACKAGES_ENABLED to false.
“Community nodes run with the same level of access as n8n itself. They can read environment variables, access the file system, make outbound network requests, and, most critically, receive decrypted API keys and OAuth tokens during workflow execution,” researchers Kiran Raj and Henrik Plate said. “There is no sandboxing or isolation between node code and the n8n runtime.”
“Because of this, a single malicious npm package is enough to gain deep visibility into workflows, steal credentials, and communicate externally without raising immediate suspicion. For attackers, the npm supply chain offers a quiet and highly effective entry point into n8n environments.”

Apple and Google have confirmed that the next version of Siri will use Gemini and Google Cloud in a multi-year collaboration between the two tech giants.
Until now, Apple has been using its own AI model for Siri, but its performance has been subpar compared to the likes of GPT, Gemini, or even Copilot.
Now, Apple and Google have entered into a multi-year collaboration. As part of this partnership, future versions of Siri will use Gemini models.

Hackers over the past six months have relied increasingly more on the browser-in-the-browser (BitB) method to trick users into providing Facebook account credentials.
The BitB phishing technique was developed by security researcher mr.d0x in 2022. Cybercriminals later adopted it in attacks targeting various online services, including Facebook and Steam.
Trellix researchers monitoring malicious activity say that threat actors steal Facebook accounts to spread scams, harvest personal data, or commit identity fraud. With more than three billion active users, the social network is still a prime target for fraudsters.