Over 60% of new CVEs are exploited within 48 hours—automation now defines who wins the cyber race.


Quantum computers, machines that process information leveraging quantum mechanical effects, could outperform classical computers on some optimization tasks and computations. Despite their potential, quantum computers are known to be prone to errors and their ability to perform computations is easily influenced by noise.
Quantum scientists and engineers have thus been developing verification protocols, tools designed to check whether quantum computers are computing information correctly. Ideally, these protocols should also provide cryptographic security, meaning that they should ensure that the information processed by computers cannot be forged or tampered with by malicious users.
Researchers at Sorbonne University, University of Edinburgh and Quantinuum recently introduced a new on-chip cryptographically secure verification protocol for quantum computers. The new protocol, outlined in a paper published in Physical Review Letters, was successfully deployed on Quantinuum’s H1-1 quantum processor.

Your conversations with AI assistants such as ChatGPT and Google Gemini may not be as private as you think they are. Microsoft has revealed a serious flaw in the large language models (LLMs) that power these AI services, potentially exposing the topic of your conversations with them. Researchers dubbed the vulnerability “Whisper Leak” and found it affects nearly all the models they tested.
When you chat with AI assistants built into major search engines or apps, the information is protected by TLS (Transport Layer Security), the same encryption used for online banking. These secure connections stop would-be eavesdroppers from reading the words you type. However, Microsoft discovered that the metadata (how your messages are traveling across the internet) remains visible. Whisper Leak doesn’t break encryption, but it takes advantage of what encryption cannot hide.

Chameleons’ wandering eyes have fascinated and puzzled scientists since the days of ancient Greece. Now, after millennia of study, modern imaging has revealed the secret of their nearly 360-degree view and uncanny ability to look in two different directions at once. Behind their bulging eyes lie two long, coiled optic nerves—a structure not seen in any other lizard.
“Chameleon eyes are like security cameras, moving in all directions,” explained Juan Daza, associate professor at Sam Houston State University and author of a new study describing the trait. “They move their eyes independently while scanning their environment to find prey. And the moment they find their prey, their eyes coordinate and go in one direction so they can calculate where to shoot their tongues.”
The authors published their study in the journal Scientific Reports.

A threat actor exploited a zero-day vulnerability in Samsung’s Android image processing library to deploy a previously unknown spyware called ‘LandFall’ using malicious images sent over WhatsApp.
The security issue was patched this year in April, but researchers found evidence that the LandFall operation was active since at least July 2024, and targeted select Samsung Galaxy users in the Middle East.
Identified as CVE-2025–21042, the zero-day is an out-of-bounds write in libimagecodec.quram.so and has a critical severity rating. A remote attacker successfully exploiting it can execute arbitrary code on a target device.

Found in everything from protein bars to energy drinks, erythritol has long been considered a safe alternative to sugar.
But research suggests this widely used sweetener may be quietly undermining one of the body’s most crucial protective barriers – with potentially serious consequences for heart health and stroke risk.
A study from the University of Colorado suggests erythritol may damage cells in the blood-brain barrier, the brain’s security system that keeps out harmful substances while letting in nutrients.
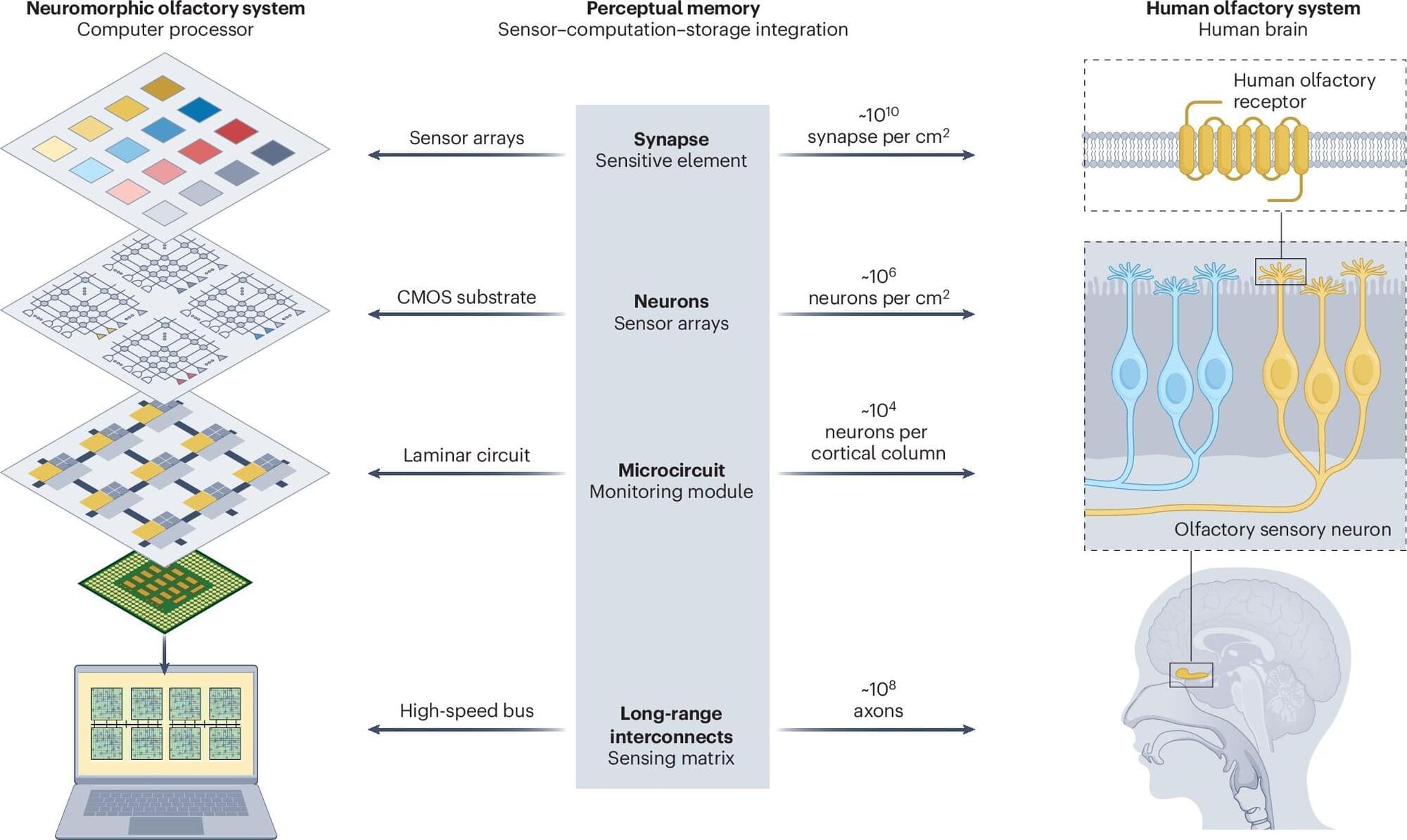
After years of trying, the electronic nose is finally making major progress in sensing smells, almost as well as its human counterpart. That is the conclusion of a scientific review into the development of neuromorphic olfactory perception chips (NOPCs), published in the journal Nature Reviews Electrical Engineering.
Evolution has perfected the human nose over millions of years. This powerful sense organ, while not the best in the animal kingdom, can still detect around a trillion smells. The quest to develop electronic noses with human nose-like abilities for applications like security, robotics, and medical diagnostics has proved notoriously difficult. So scientists have increasingly been turning to neuromorphic computing, which involves designing software and hardware that mimics the structure and function of the human nose.
In this review, a team of scientists from China highlights some of the key advances in developing olfactory sensing chips. The paper focuses heavily on gas sensors because they are key components of the electronic nose system. They must physically detect odor molecules and convert them into electrical signals.
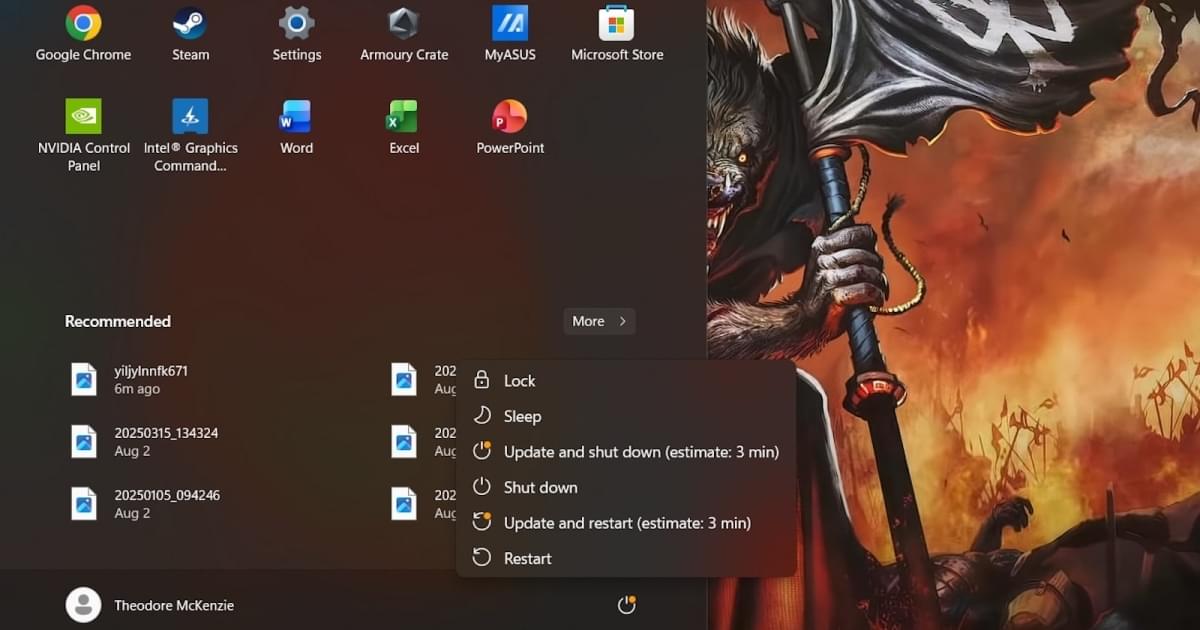
For Mac/Linux users out there who might not be familiar, the bug in question would cause your PC to randomly restart after clicking the “Update and shut down” button, leaving many users wondering if they had accidentally chosen the wrong option. While largely harmless, it became one of the most infamous errors in Microsoft’s OS due to its sheer annoyance and the company’s apparent reluctance to address it for nearly a decade, with some users reporting it as far back as eight years ago in Windows 10.
Marking the end of an era of sorts, the KB5067036 non-security update for Windows 11 has finally resolved the bug, with Microsoft fixing the “underlying issue” that prevented the “Update and shut down” button from actually shutting down your PC. Moreover, the new version also tackles the bug that could cause Windows Update to fail with error 0x800f0983, hopefully making the process of updating your PC a bit less cumbersome.

Security Operations Centers (SOC) today are overwhelmed. Analysts handle thousands of alerts every day, spending much time chasing false positives and adjusting detection rules reactively. SOCs often lack the environmental context and relevant threat intelligence needed to quickly verify which alerts are truly malicious. As a result, analysts spend excessive time manually triaging alerts, the majority of which are classified as benign.
Addressing the root cause of these blind spots and alert fatigue isn’t as simple as implementing more accurate tools. Many of these traditional tools are very accurate, but their fatal flaw is a lack of context and a narrow focus — missing the forest for the trees. Meanwhile, sophisticated attackers exploit exposures invisible to traditional reactive tools, often evading detection using widely-available bypass kits.
While all of these tools are effective in their own right, they often fail because of the reality that attackers don’t employ just one attack technique, exploit just one type of exposure or weaponize a single CVE when breaching an environment. Instead, attackers chain together multiple exposures, utilizing known CVEs where helpful, and employing evasion techniques to move laterally across an environment and accomplish their desired goals. Individually, traditional security tools may detect one or more of these exposures or IoCs, but without the context derived from a deeply integrated continuous exposure management program, it can be nearly impossible for security teams to effectively correlate otherwise seemingly disconnected signals.
