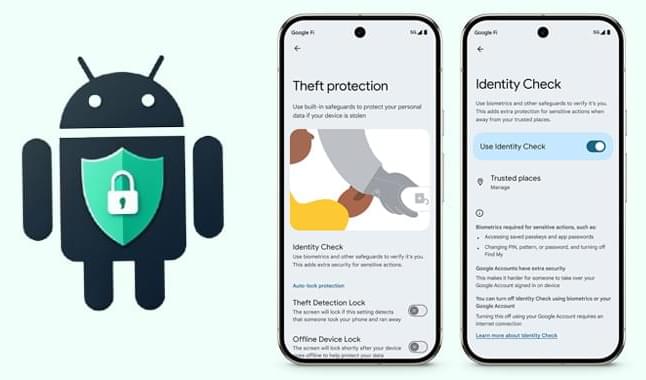
Google’s Identity Check locks sensitive Android settings behind biometrics, enhancing security outside trusted locations.


The RealHome theme and the Easy Real Estate plugins for WordPress are vulnerable to two critical severity flaws that allow unauthenticated users to gain administrative privileges.
Although the two flaws were discovered in September 2024 by Patchstack, and multiple attempts were made to contact the vendor (InspiryThemes), the researchers say they have not received a response.
Also, Patchstack says the vendor released three versions since September, but no security fixes to address the critical issues were introduced. Hence, the issues remain unfixed and exploitable.

A security researcher discovered a flaw in Cloudflare’s content delivery network (CDN), which could expose a person’s general location by simply sending them an image on platforms like Signal and Discord.
While the geo-locating capability of the attack is not precise enough for street-level tracking, it can provide enough data to infer what geographic region a person lives in and monitor their movements.
Daniel’s finding is particularly concerning for people who are highly concerned about their privacy, like journalists, activists, dissidents, and even cybercriminals.
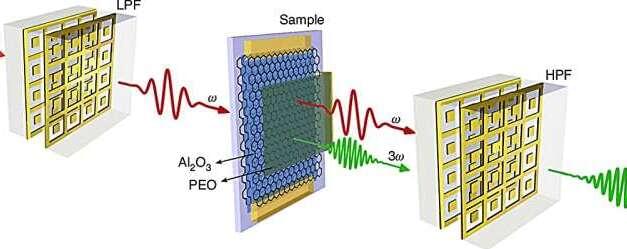
A team of researchers from the University of Ottawa has developed innovative methods to enhance frequency conversion of terahertz (THz) waves in graphene-based structures, unlocking new potential for faster, more efficient technologies in wireless communication and signal processing.
THz waves, located in the far-infrared region of the electromagnetic spectrum, can be used to perform non-invasive imaging through opaque materials for security and quality control applications. Additionally, these waves hold great promise for wireless communication.
Advances in THz nonlinear optics, which can be used to change the frequency of electromagnetic waves, are essential for the development of high-speed wireless communication and signal processing systems for 6G technologies and beyond.

In today’s AI news, a new $500 billion, private sector investment to build artificial intelligence infrastructure in the US, with Oracle, ChatGPT creator OpenAI, and Japanese conglomerate SoftBank among those committing to the project. The joint venture, called Stargate, is expected to begin with a data center project in Texas.
In other advancements, Perplexity has launched an aggressive bid to capture the enterprise AI search market, unveiling Sonar, an API service that outperforms offerings from Google, OpenAI and Anthropic on key benchmarks while also undercutting their prices. Perplexity — now valued at $9 billion — directly challenges larger competitors.
And, Santee Cooper, the big power provider in South Carolina, has tapped financial advisers to look for buyers that can restart construction on a pair of nuclear reactors that were mothballed years ago. The state-owned utility is betting interest will be strong, with tech giants such as Amazon and Microsoft in need of clean energy to fuel AI.
Then, Google is making a fresh investment of more than $1 billion into AI startup Anthropic, the Financial Times reported on Wednesday. This comes after Reuters and other media reported earlier in January that Anthropic was nearing a $2 billion fundraise in a round, led by Lightspeed Venture Partners, valuing the firm at about $60 billion.
In videos, Indeed CEO Chris Hyams, and Stanford Digital Economy Lab Director Erik Brynjolfsson, join Bloomberg’s Work for a discussion on the key trends impacting employees and employers in 2025 and beyond.
Meanwhile, Sarah Friar, Chief Financial Officer of OpenAI warned that there is strong competition in the development of AI coming from China, recognizing the economic and security benefits of the emerging technology.
S Shirin Ghaffary at Bloomberg House in Davos. ‘ + s Erik Schatzker at Bloomberg House in Davos. + ll look at how Frames offers cinematic image outputs, best practices for prompting, and showcases user-generated examples. + Thats all for today, but AI is moving fast, subscribe today to stay informed. Please don’t forget to vote for me in the Entrepreneur of Impact Competition today! Thank you for supporting me and my partners, it’s how I keep NNN free.

The Stargate Project is a new company which intends to invest $500 billion over the next four years building new AI infrastructure for OpenAI in the United States. We will begin deploying $100 billion immediately. This infrastructure will secure American leadership in AI, create hundreds of thousands of American jobs, and generate massive economic benefit for the entire world. This project will not only support the re-industrialization of the United States but also provide a strategic capability to protect the national security of America and its allies.
The initial equity funders in Stargate are SoftBank, OpenAI, Oracle, and MGX. SoftBank and OpenAI are the lead partners for Stargate, with SoftBank having financial responsibility and OpenAI having operational responsibility. Masayoshi Son will be the chairman.
Arm, Microsoft, NVIDIA, Oracle, and OpenAI are the key initial technology partners. The buildout is currently underway, starting in Texas, and we are evaluating potential sites across the country for more campuses as we finalize definitive agreements.

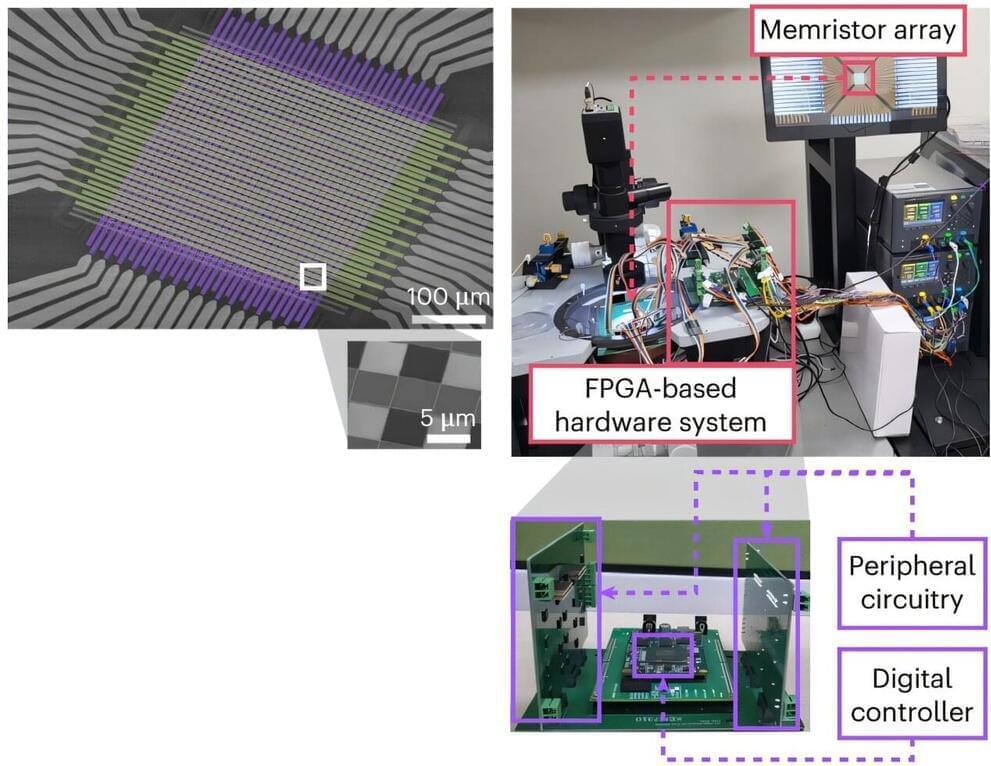
Existing computer systems have separate data processing and storage devices, making them inefficient for processing complex data like AI. A KAIST research team has developed a memristor-based integrated system similar to the way our brain processes information. It is now ready for application in various devices, including smart security cameras, allowing them to recognize suspicious activity immediately without having to rely on remote cloud servers, and medical devices with which it can help analyze health data in real time.
The joint research team of Professor Shinhyun Choi and Professor Young-Gyu Yoon of the School of Electrical Engineering has developed the next-generation neuromorphic semiconductor-based ultra-small computing chip that can learn and correct errors on its own. The research is published in the journal Nature Electronics.
What is special about this computing chip is that it can learn and correct errors that occur due to non-ideal characteristics that were difficult to solve in existing neuromorphic devices. For example, when processing a video stream, the chip learns to automatically separate a moving object from the background, and it becomes better at this task over time.