Can I sign up to go to the moon? It might be easier than trying to get a better 4G here on planet Earth.


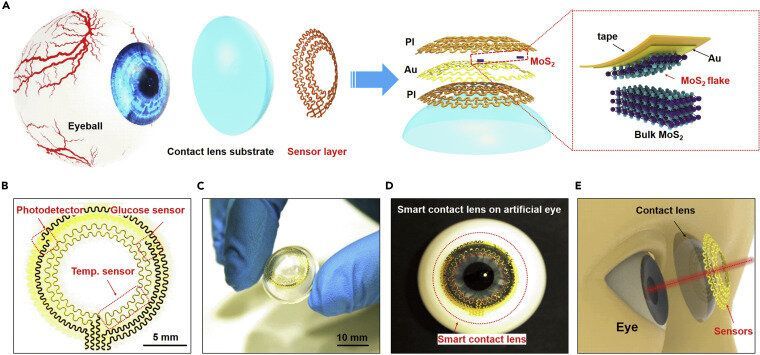
The enormous impact of the recent COVID-19 pandemic, together with other diseases or chronic health risks, has significantly prompted the development and application of bioelectronics and medical devices for real-time monitoring and diagnosing health status. Among all these devices, smart contact lenses attract extensive interests due to their capability of directly monitoring physiological and ambient information. Smart contact lenses equipped with high sensitivity sensors would open the possibility of a non-invasive method to continuously detect biomarkers in tears. They could also be equipped with application-specific integrated circuit chips to further enrich their functionality to obtain, process and transmit physiological properties, manage illnesses and health risks, and finally promote health and wellbeing. Despite significant efforts, previous demonstrations still need multistep integration processes with limited detection sensitivity and mechanical biocompatibility.
Recently, researchers from the University of Surrey, National Physical Laboratory (NPL), Harvard University, University of Science and Technology of China, Zhejiang University Ningbo Research Institute, etc. have developed a multifunctional ultrathin contact lens sensor system. The sensor systems contain a photodetector for receiving optical information, imaging and vision assistance, a temperature sensor for diagnosing potential corneal disease, and a glucose sensor for monitoring glucose level directly from the tear fluid.
Dr. Yunlong Zhao, Lecturer in Energy Storage and Bioelectronics at the Advanced Technology Institute (ATI), University of Surrey and Senior Research Scientist at the UK National Physical Laboratory (NPL), who led this research stated, “These results provide not only a novel and easy-to-make method for manufacturing advanced smart contact lenses but also a novel insight of designing other multifunctional electronics for Internet of Things, human machine interface, etc.” Dr. Zhao added, “our ultrathin transistors-based serpentine mesh sensor system and fabrication strategy allow for further incorporation of other functional components, such as electrode array for electrophysiology, antennas for wireless communication, and the power modules, e.g. thin-film batteries and enzymatic biofuel cell for future in vivo exploration and practical application. Our research team at ATI, University of Surrey and NPL are currently working on these fields.”

Before the century is out, advances in nanotechnology, nanomedicine, AI, and computation will result in the development of a “Human Brain/Cloud Interface” (B/CI), that connects neurons and synapses in the brain to vast cloud-computing networks in real time.
That’s the prediction of a large international team of neurosurgeons, roboticists, and nanotechnologists, writing in the journal Frontiers in Neuroscience.
A Human Brain/Cloud Interface, sometimes dubbed the “internet of thoughts”, theoretically links brains and cloud-based data storage through the intercession of nanobots positioned at strategically useful neuronal junctions.
Scientists are edging closer to making a super-secure, super-fast quantum internet possible: they’ve now been able to ‘teleport’ high-fidelity quantum information over a total distance of 44 kilometres (27 miles).
Both data fidelity and transfer distance are crucial when it comes to building a real, working quantum internet, and making progress in either of these areas is cause for celebration for those building our next-generation communications network.
In this case the team achieved a greater than 90 percent fidelity (data accuracy) level with its quantum information, as well as sending it across extensive fibre optic networks similar to those that form the backbone of our existing internet.
While many institutions are developing quantum computers, making a quantum internet requires a way to transfer the information between computers. This is accomplished by a phenomenon called quantum teleportation, in which two atoms separated by large distances are made to act as if they are identical.
Don Lincoln writes about recent research that has brought us closer to actualizing the goal of a quantum internet, giving us both hope and fear about what it could mean for the future.

Are you fed up with all the negativity?
Between Tesla, SpaceX (Starship & Starlink), 5G, mRNA vaccines and more, 2020 has been an eventful year full of breakthroughs all set to make our lives better, and ushering in a sci-fi future quicker than ever…so I brought them all together in one video to celebrate the great people working tirelessly to make our future better.
If you want a feel good boost, why not drop by and spend a few mins revelling in the positive stories of 2020.
Have an awesome New Year!!
In Looking Back At 2020 I want to review the year to show that for all the bad, there was still some amazing good and positive stories that refused to take a back seat.
A viable quantum internet—a network in which information stored in qubits is shared over long distances through entanglement—would transform the fields of data storage, precision sensing and computing, ushering in a new era of communication.
This month, scientists at Fermi National Accelerator Laboratory—a U.S. Department of Energy national laboratory affiliated with the University of Chicago—along with partners at five institutions took a significant step in the direction of realizing a quantum internet.
In a paper published in PRX Quantum, the team presents for the first time a demonstration of a sustained, long-distance teleportation of qubits made of photons (particles of light) with fidelity greater than 90%.

For those of us who don’t think that even our bowel movements will soon be inventoried, tracked and timestamped during every moment of existence, here is a just published white paper from the Rand Corporation, an influential think tank created in 1948 to offer research and analysis to the US military, which begs to differ.
The November 2020 whilte paper, published under the title “The Internet of Bodies,” focuses on the advantages and disadvantages, security and privacy risks, plus the ethical implications of what it calls a growing “Internet of Bodies (IoB).”
IoB tools are internet-connected “smart” devices increasingly available in the marketplace which promise to track and upload to the internet measurements related to individual heartbeat, blood pressure and other bodily functions in real time for purposes of health, exercise, security or other reasons.

This doesn’t sound good. 😃
The scientists put hundreds of participants through memory and cognitive tasks as well as brain scans, according to the research, published last month in the journal World Psychiatry.
Joseph Firth, the Western Sydney University scientist who led the project, described in a press release how the internet’s design is changing both the structure and abilities of the human brain.
The “limitless stream of prompts and notifications from the Internet encourages us towards constantly holding a divided attention,” said Firth, “which then in turn may decrease our capacity for maintaining concentration on a single task.”