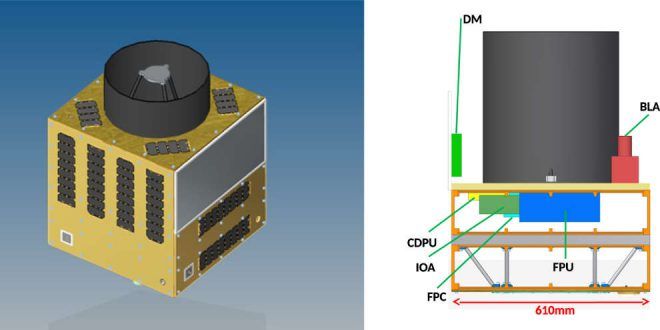
Quantum theory predicts that a vast number of atoms can be entangled and intertwined by a very strong quantum relationship, even in a macroscopic structure. Until now, however, experimental evidence has been mostly lacking, although recent advances have shown the entanglement of 2,900 atoms. Scientists at the University of Geneva (UNIGE), Switzerland, recently reengineered their data processing, demonstrating that 16 million atoms were entangled in a one-centimetre crystal. They have published their results in Nature Communications.
The laws of quantum physics allow immediately detecting when emitted signals are intercepted by a third party. This property is crucial for data protection, especially in the encryption industry, which can now guarantee that customers will be aware of any interception of their messages. These signals also need to be able to travel long distances using special relay devices known as quantum repeaters—crystals enriched with rare earth atoms and cooled to 270 degrees below zero (barely three degrees above absolute zero), whose atoms are entangled and unified by a very strong quantum relationship. When a photon penetrates this small crystal block, entanglement is created between the billions of atoms it traverses. This is explicitly predicted by the theory, and it is exactly what happens as the crystal re-emits a single photon without reading the information it has received.
It is relatively easy to entangle two particles: Splitting a photon, for example, generates two entangled photons that have identical properties and behaviours. Florian Fröwis, a researcher in the applied physics group in UNIGE’s science faculty, says, “But it’s impossible to directly observe the process of entanglement between several million atoms since the mass of data you need to collect and analyse is so huge.”