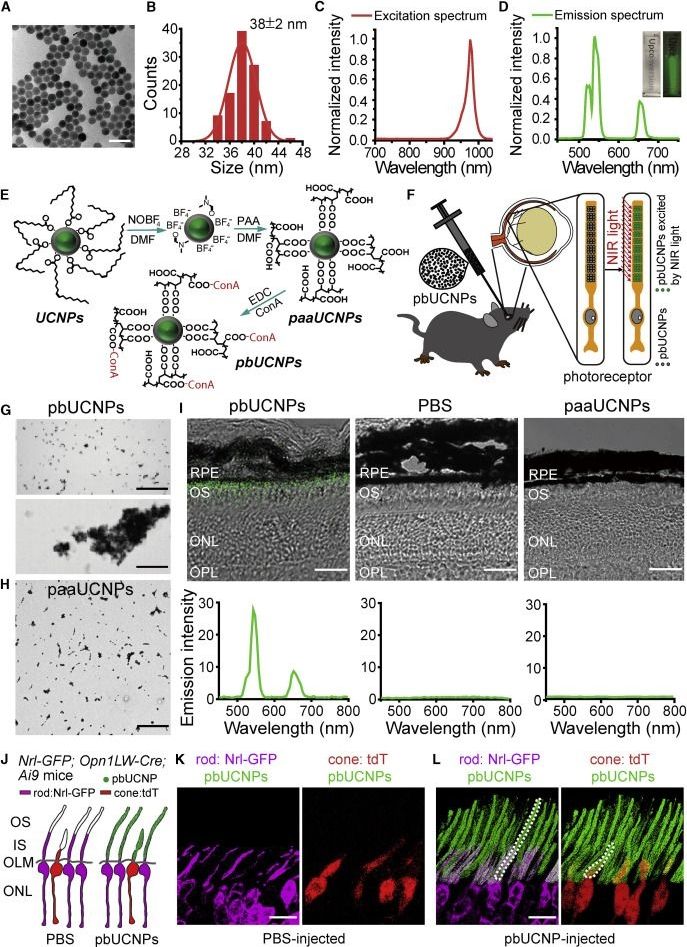
Mice with vision enhanced by nanotechnology were able to see infrared light as well as visible light, reports a study published February 28 in the journal Cell. A single injection of nanoparticles in the mice’s eyes bestowed infrared vision for up to 10 weeks with minimal side effects, allowing them to see infrared light even during the day and with enough specificity to distinguish between different shapes. These findings could lead to advancements in human infrared vision technologies, including potential applications in civilian encryption, security, and military operations.
Injectable photoreceptor-binding nanoparticles with the ability to convert photons from low-energy to high-energy forms allow mice to develop infrared vision without compromising their normal vision and associated behavioral responses.