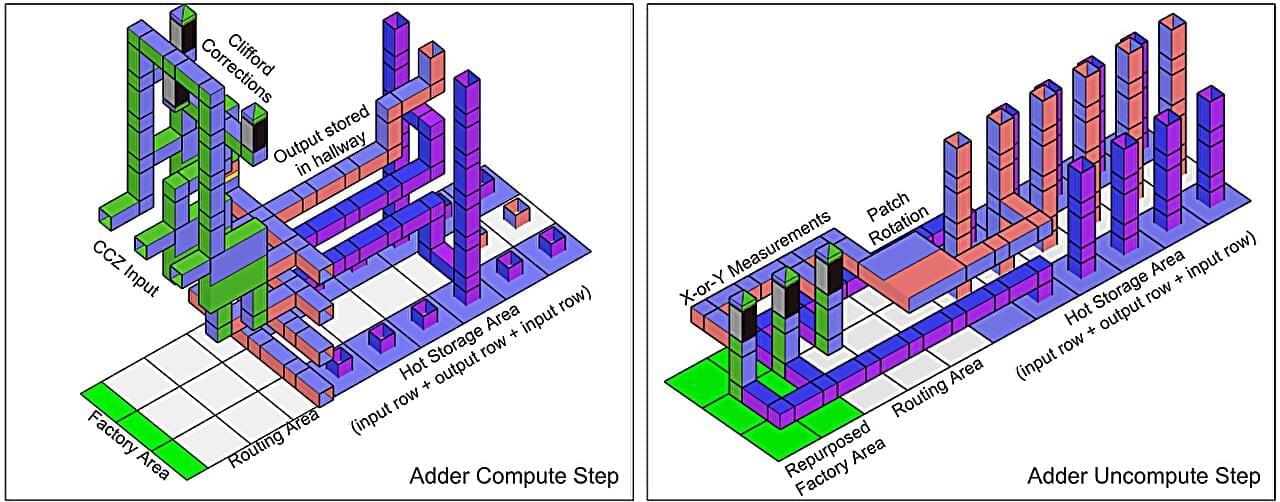
A team of researchers at AI Google Quantum AI, led by Craig Gidney, has outlined advances in quantum computer algorithms and error correction methods that could allow such computers to crack Rivest–Shamir–Adleman (RSA) encryption keys with far fewer resources than previously thought. The development, the team notes, suggests encryption experts need to begin work toward developing next-generation encryption techniques. The paper is published on the arXiv preprint server.
RSA is an encryption technique developed in the late 1970s that involves generating public and private keys; the former is used for encryption and the latter decryption. Current standards call for using a 2,048-bit encryption key. Over the past several years, research has suggested that quantum computers would one day be able to crack RSA encryption, but because quantum development has been slow, researchers believed that it would be many years before it came to pass.
Some in the field have accepted a theory that a quantum computer capable of cracking such codes in a reasonable amount of time would have to have at least 20 million qubits. In this new work, the team at Google suggests it could theoretically be done with as few as a million qubits—and it could be done in a week.