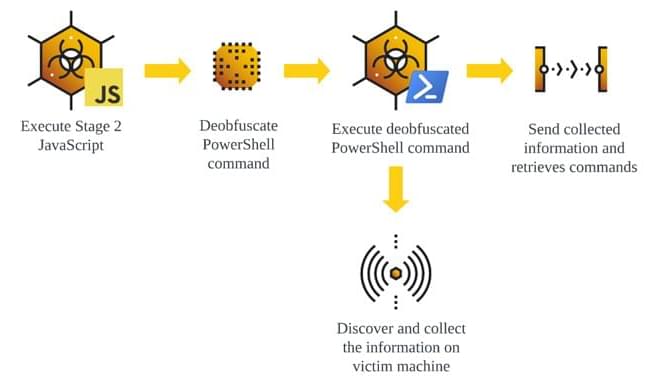
Play ransomware’s new Linux variant targets VMWare ESXi, expanding its reach. US leads in victims, with manufacturing and services most affected.



Computer security company CrowdStrike is linked to a major IT outage affecting banks, airports, supermarkets and businesses across Australia and the world.
Airport check-in systems across the globe have been disrupted and businesses have reported the “blue screen of death” and IT outages.
Follow our live blog or download the ABC News app and subscribe to our range of news alerts for the latest updates.


Related: High-G data recorder helps Air Force munitions testing
The Army wants a company to build and deliver MDAC prototypes using existing fielded and mature technologies. MDAC will be air-, rail-, and sea-transportable per MIL-STD-1366; will be able to move rapidly for survivability; have automated high rates of fire with HVP; and have emote weapon firing; have deep magazine capacity, rapid ammunition resupply, and high operational availability. Companies interested also will demonstrate supportability, safety, and cyber security.
JAXA has not said who the attackers were, but most cybersecurity observers are pointing the finger at state actors working for China.
“The fact that a space agency was targeted with a sophisticated complex attack indicates a state actor with goals to compromise data, not just gather intelligence or send a political message, with the lead suspect being a China affiliated cyber security private company of some sort,” said Irina Tsukerman, a geopolitical analyst and the president of Scarab Rising, a global strategy advisory firm. “Such an attack is likely the work of either a state-backed independent hacker, possibly part of an intelligence gathering gang, whose methods could potentially be analyzed and compared to prior such attacks, or it could be attributed to a private cybersecurity company, most likely affiliated with China, in which case prior incidents could be harder to detect. The most interesting detail was the description of the attack and the fact that the attacker used several different types of malware and nevertheless went undetected.

The call and text message records from mid-to-late 2022 of tens of millions of AT&T cellphone customers and many non-AT&T customers were exposed in a massive data breach, the telecom company revealed Friday.
AT&T said the compromised data includes the telephone numbers of “nearly all” of its cellular customers and the customers of wireless providers that use its network between May 1, 2022 and October 31, 2022.
The stolen logs also contain a record of every number AT&T customers called or texted – including customers of other wireless networks – the number of times they interacted, and the call duration.
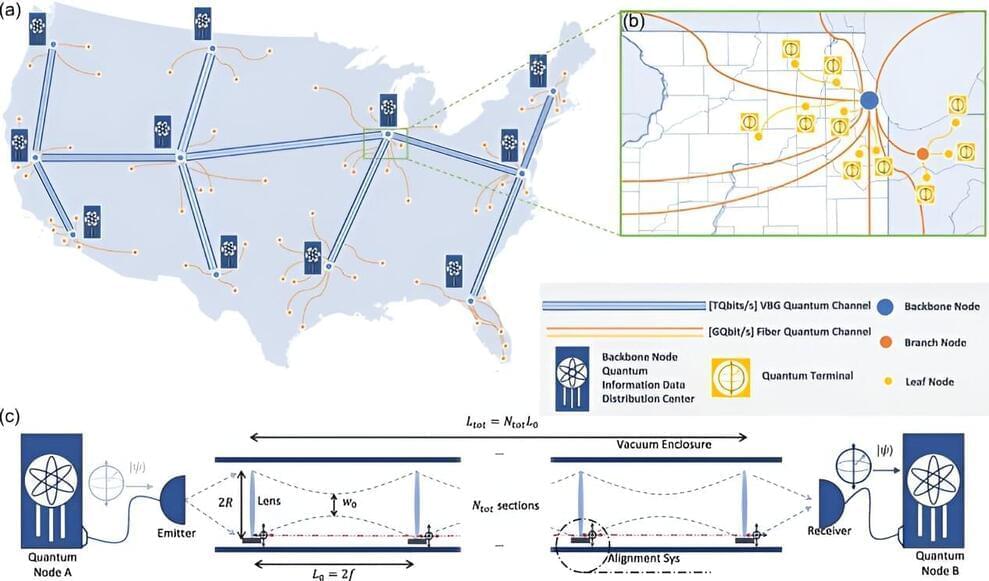
Quantum computers offer powerful ways to improve cybersecurity, communications, and data processing, among other fields. To realize these full benefits, however, multiple quantum computers must be connected to build quantum networks or a quantum internet. Scientists have struggled to come up with practical methods of building such networks, which must transmit quantum information over long distances.
Now, researchers at the University of Chicago Pritzker School of Molecular Engineering (PME) have proposed a new approach—building long quantum channels using vacuum sealed tubes with an array of spaced-out lenses. These vacuum beam guides, about 20 centimeters in diameter, would have ranges of thousands of kilometers and capacities of more than 1,013 qubits per second, better than any existing quantum communication approach. Photons of light encoding quantum data would move through the vacuum tubes and remain focused thanks to the lenses.
“We believe this kind of network is feasible and has a lot of potential,” said Liang Jiang, professor of molecular engineering and senior author of the new work. “It could not only be used for secure communication, but also for building distributed quantum computing networks, distributed quantum sensing technologies, new kinds of telescopes, and synchronized clocks.”