Discover Zergeca, a new sophisticated botnet capable of DDoS attacks and more. Learn about its features, targets, and potential impact on cybersecurit.




Conventional encryption methods rely on complex mathematical algorithms and the limits of current computing power. However, with the rise of quantum computers, these methods are becoming increasingly vulnerable, necessitating quantum key distribution (QKD).
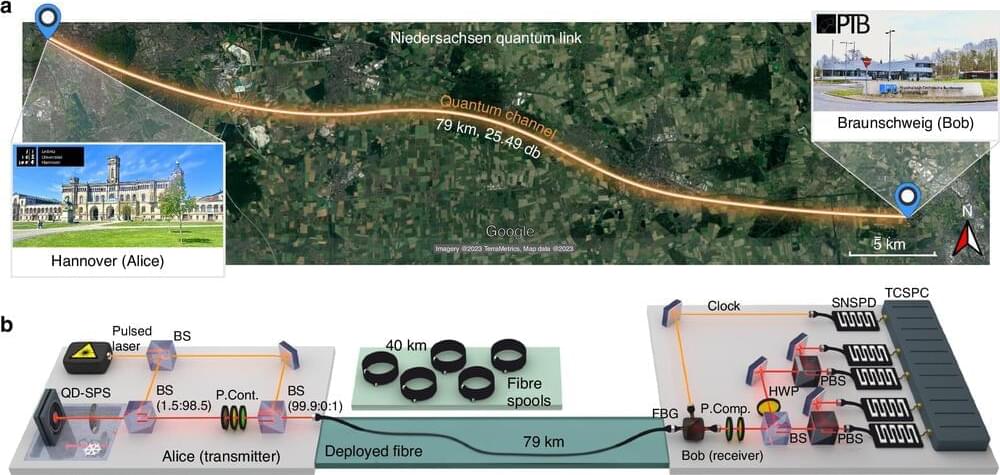
QKD is a technology that leverages the unique properties of quantum physics to secure data transmission. This method has been continuously optimized over the years, but establishing large networks has been challenging due to the limitations of existing quantum light sources.
In a new article published in Light: Science & Applications, a team of scientists in Germany have achieved the first intercity QKD experiment with a deterministic single-photon source, revolutionizing how we protect our confidential information from cyber threats.

Cisco has patched an NX-OS zero-day exploited in April attacks to install previously unknown malware as root on vulnerable switches.
Cybersecurity firm Sygnia, who reported the incidents to Cisco, linked the attacks to a Chinese state-sponsored threat actor it tracks as Velvet Ant.
“Sygnia detected this exploitation during a larger forensic investigation into the China-nexus cyberespionage group we are tracking as Velvet Ant,” Amnon Kushnir, Director of Incident Response at Sygnia, told BleepingComputer.
An interesting way of punishment.



Star Trek: The Next Generation looks at sentience as consciousness, self-awareness, and intelligence—and that was actually pretty spot on. Sentience is the innate human ability to experience feelings and sensations without association or interpretation. “We’re talking about more than just code; we’re talking about the ability of a machine to think and to feel, along with having morality and spirituality,” Ishaani Priyadarshini, a Cybersecurity Ph.D. candidate from the University of Delaware, tells Popular Mechanics.
💡AI is very clever and able to mimic sentience, but never actually become sentient itself.
The very idea of consciousness has been heavily contested in philosophy for decades. The 17th-century philosopher René Descartes famously said, “I think therefore I am.” A simple statement on the surface, but it was the result of his search for a statement that couldn’t be doubted. Think about it: he couldn’t doubt his existence as he was the one doubting himself in the first place.