Deleting another spam email in our inbox is becoming an everyday habit. Some may have even had their accounts hacked after clicking a misleading link or had their identities stolen. These are some common cybercrimes and as our reliance on the internet grows, our interactions with cybercrimes becomes more frequent.
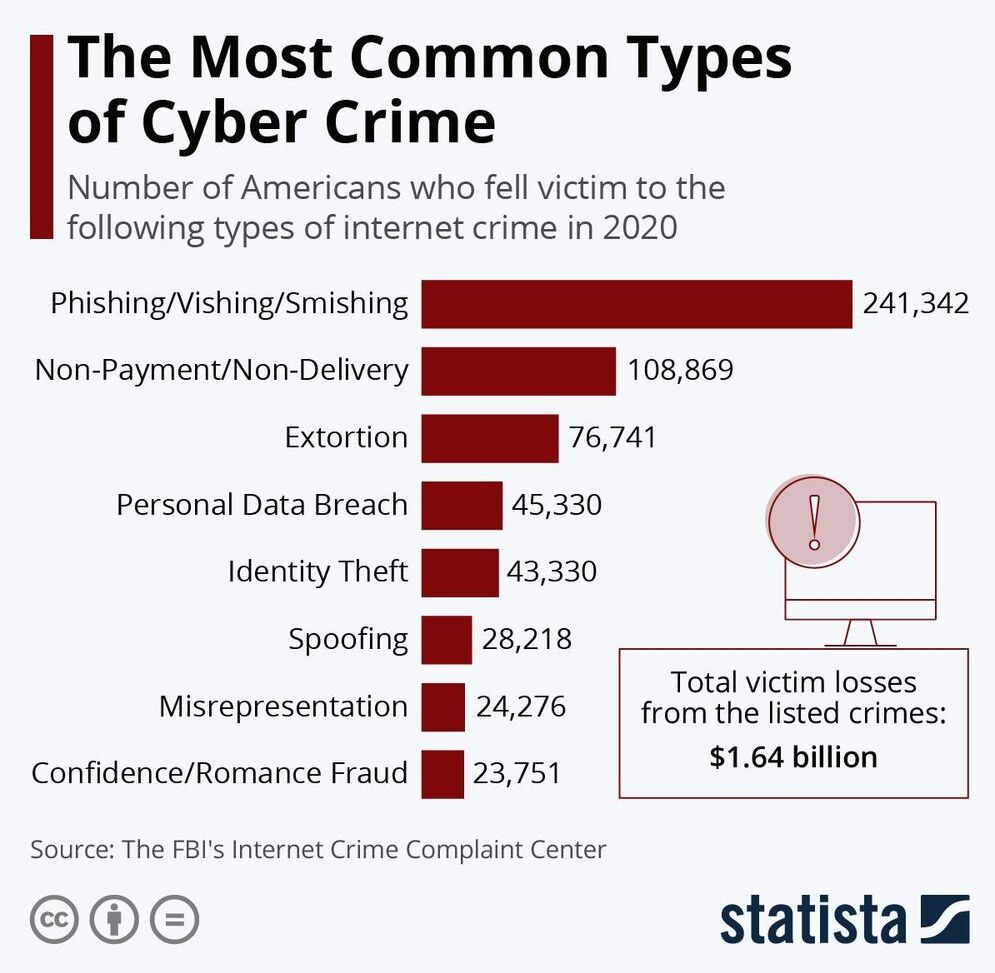
According to a recent FBI report on internet crime, 241342 Americans fell victim to phishing, vishing (via call) and smishing (via text) attacks last year, making it the most common type of cybercrime.
This chart shows the most common types of internet crimes in the U.S. in 2020.