Protect yourself and your organization from the threat of unknown malware. Check out this guide to detecting suspicious behavior.



An open source command-and-control (C2) framework known as Havoc is being adopted by threat actors as an alternative to other well-known legitimate toolkits like Cobalt Strike, Sliver, and Brute Ratel.
Cybersecurity firm Zscaler said it observed a new campaign in the beginning of January 2023 targeting an unnamed government organization that utilized Havoc.
“While C2 frameworks are prolific, the open-source Havoc framework is an advanced post-exploitation command-and-control framework capable of bypassing the most current and updated version of Windows 11 defender due to the implementation of advanced evasion techniques such as indirect syscalls and sleep obfuscation,” researchers Niraj Shivtarkar and Niraj Shivtarkar said.

A new variant of the notorious Mirai botnet has been found leveraging several security vulnerabilities to propagate itself to Linux and IoT devices.
Observed during the second half of 2022, the new version has been dubbed V3G4 by Palo Alto Networks Unit 42, which identified three different campaigns likely conducted by the same threat actor.
“Once the vulnerable devices are compromised, they will be fully controlled by attackers and become a part of the botnet,” Unit 42 researchers said. “The threat actor has the capability to utilize those devices to conduct further attacks, such as distributed denial-of-service (DDoS) attacks.”
Scientists have taken a key step toward harnessing a form of artificial intelligence known as deep reinforcement learning, or DRL, to protect computer networks.
When faced with sophisticated cyberattacks in a rigorous simulation setting, deep reinforcement learning was effective at stopping adversaries from reaching their goals up to 95 percent of the time. The outcome offers promise for a role for autonomous AI in proactive cyber defense.
Scientists from the Department of Energy’s Pacific Northwest National Laboratory documented their findings in a research paper and presented their work Feb. 14 at a workshop on AI for Cybersecurity during the annual meeting of the Association for the Advancement of Artificial Intelligence in Washington, D.C.
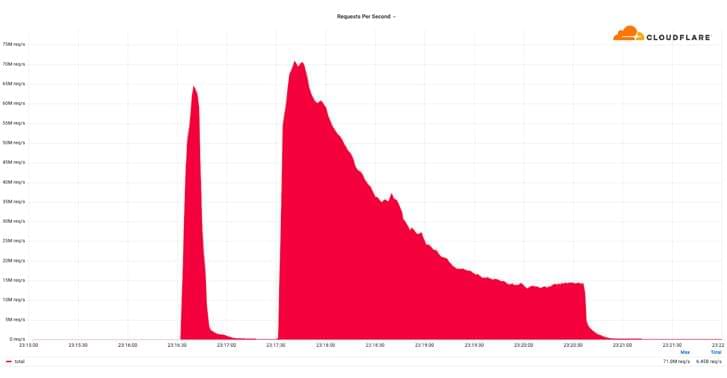
Web infrastructure company Cloudflare on Monday disclosed that it thwarted a record-breaking distributed denial-of-service (DDoS) attack that peaked at over 71 million requests per second (RPS).
“The majority of attacks peaked in the ballpark of 50–70 million requests per second (RPS) with the largest exceeding 71 million,” the company said, calling it a “hyper-volumetric” DDoS attack.
It’s also the largest HTTP DDoS attack reported to date, more than 35% higher than the previous 46 million RPS DDoS attack that Google Cloud mitigated in June 2022.

Science fiction has become a reality with recent developments toward biohacking through nanotechnology. Soon, science and industries may soon realize the potential of human hacking… but at what risk versus reward? Medical nanotechnology is one of these such topics. Many experts believe nanotechnology will pave the way for a bright, new future in improving our wellbeing. Yet, at the core of this biohacking are machines and as we’ve seen with other technologies — there are very real risks of malicious intent. In this video, we share some of the applications being developed combining nanotechnology and medicine. We also look at the potential risks found in the practice and how we may mitigate issues before they’re problematic. We also share how companies can reduce security flaws and curb public perception so the nanotechnology industry can flourish without major setbacks. Want to learn more about this budding area of science and medicine?
See our accompanying blog post for the details and be sure to dig around the site, here:
#nanotech #nanotechhacking
Top 10 upcoming future technologies | trending technologies | 10 upcoming tech.
Future technologies are currently developing at an acclerated rate. Future technology ideas are being converted into real life at a very fast pace.
These Innovative techs will address global challenges and at the same time will make life simple on this planet. Let’s get started and have a look at the top technologies of the future | Emerging technologies.
#futuretechnologies #futuretech #futuristictechnologys #emergingtechnologies #technology #tech #besttechnology #besttech #newtechnology #cybersecurity #blockchain #emergingtech #futuretechnologyideas #besttechnologies #innovativetechs.
Chapters.
00:00 ✅ Intro.
00:23 ✅ 10. Genomics: Device to improve your health.
01:13 ✅ 09. New Energy Solutions for the benefit of our environment.
01:53 ✅ 08. Robotic Process Automation: Technology that automates jobs.
02:43 ✅ 07. Edge Computing to tackle limitations of cloud computing.
03:39 ✅ 06. Quantum Computing: Helping to stop the spread of diseases.
04:31 ✅ 05. Augmented reality and virtual reality: Now been employed for training.
05:05 ✅ 04. Blockchain: Delivers valuable security.
05:50 ✅ 03. Internet of things: So many things can connect to the internet and to one another.
06:40 ✅ 02. Cyber Security to improve security.
07:24 ✅ 01. 3D Printing: Used to create prototypesfuturistic technologybest future tech.
Here at Tech Buzzer, we ensure that you are continuously in touch with the latest update and aware of the foundation of the tech industry. Thank you for being with us. Please subscribe to our channel and enjoy the ride.
Are we dabbling in dangerous waters by advancing artificial intelligence? As we continue to push the boundaries of technology and artificial intelligence, it’s important to consider the potential consequences. In this video, we’ll explore the dangers of conscious AI as seen through the lens of Musk’s warnings and proposed solutions. In today’s video we look at Elon Musk on the Dangers of Artificial Intelligence…Keep watching to see artificial intelligence and elon musk artificial intelligence and of course elon musk on artificial intelligence and the steep dangers of artificial intelligence and to be aware of artificial intelligence and elon musk on AI and the dangers of artificial intelligence and artificial intelligence is dangerous and of course artificial general intelligence and artificial intelligence documentary and the artificial intelligence danger and sophia the robot artificial intelligence and the future of artificial intelligence Subscribe for Artificial Intelligence, Data Science, and Tech. Inspired by Tech Vision, Moconomy, and Digital Engine. Inspired by Experts say she will end humanity. Here’s the fix, with Elon Musk, ChatGPT, AI robots. Inspired by Japanese Killer Robots Murder 29 Scientists | Elon Musk Warned Us About ThisInspired by Elon Musk Released Terrifying Details About The Tesla AI BotInspired by Elon Musk’s Last Warning About Artificial IntelligenceInspired by “I Tried To Warn You” — Elon Musk LAST WARNING (2023)Also check out: https://youtu.be/ywST4J656kQOn Technology Titan we will go through Artificial Intelligence, Crypto, and Technology. Stay tuned for the latest AI, SpaceX, and Cyber Security. Click here to subscribe: bit.ly/3WvpXbT